How To Secure Nginx From Clickjack attack using X-Frame-Options
Explains the way to secure websites and web-based applications from Clickjacking hosted on Nginx Web Server using the Header option X-Frame-Options.
Clickjacking, also known as UI redress attack is one of the well-known vulnerabilities of websites and web-based applications. It's used by the attacker to force the user to click without user consent, leading to redirection to unknown websites.
This tutorial explains the steps required to secure the websites and web-based applications from Clickjacking by using the X-Frame-Options header directives. The directives provide instructions to browsers to allow or disallow iframes, preventing content from other sites.
The possible directives available with X-Frame-Options are listed below. These can be added either to the
You can also follow the tutorials How To Install And Configure Nginx on Ubuntu 18.04 LTS and Configure Virtual Host Or Server Block On Nginx.
SAMEORIGIN
Allow iframes from the same origin i.e. the same Nginx server used to host the website. We need to update the
// http - Add same origin policy to allow iframes from same server and reload the server
sudo nano /etc/nginx/nginx.conf
# Update the http block
http {
include /etc/nginx/mime.types;
default_type application/octet-stream;
....
....
#gzip on;
include /etc/nginx/conf.d/*.conf;
include /etc/nginx/sites-enabled/*;
# X-Frame-Options
add_header X-Frame-Options sameorigin always;
}
# Save and exit the editor
# Check configurations
sudo nginx -t
# Reload configuration
sudo systemctl reload nginx
Instead of enabling it for all the server blocks, we can enable it for a specific server block as shown below.
# Update server block
sudo nano /etc/nginx/sites-available/example.com
# Content
server {
listen 80;
server_name example.com www.example.com;
# X-Frame-Options
add_header X-Frame-Options sameorigin always;
...
...
}
# Save and exit the editor
# Check configurations
sudo nginx -t
# Reload configuration
sudo systemctl reload nginx
Similarly, we can also add it to the specific location block instead of enabling it for the entire site or application. It can be done as shown below.
# Update server block
sudo nano /etc/nginx/sites-available/example.com
# Content
server {
listen 80;
server_name example.com www.example.com;
....
....
location / {
....
....
# X-Frame-Options
add_header X-Frame-Options sameorigin always;
...
...
}
...
...
}
# Save and exit the editor
# Check configurations
sudo nginx -t
# Reload configuration
sudo systemctl reload nginx
The difference without and with X-Frame-Options is shown in Fig 1 and Fig 2.
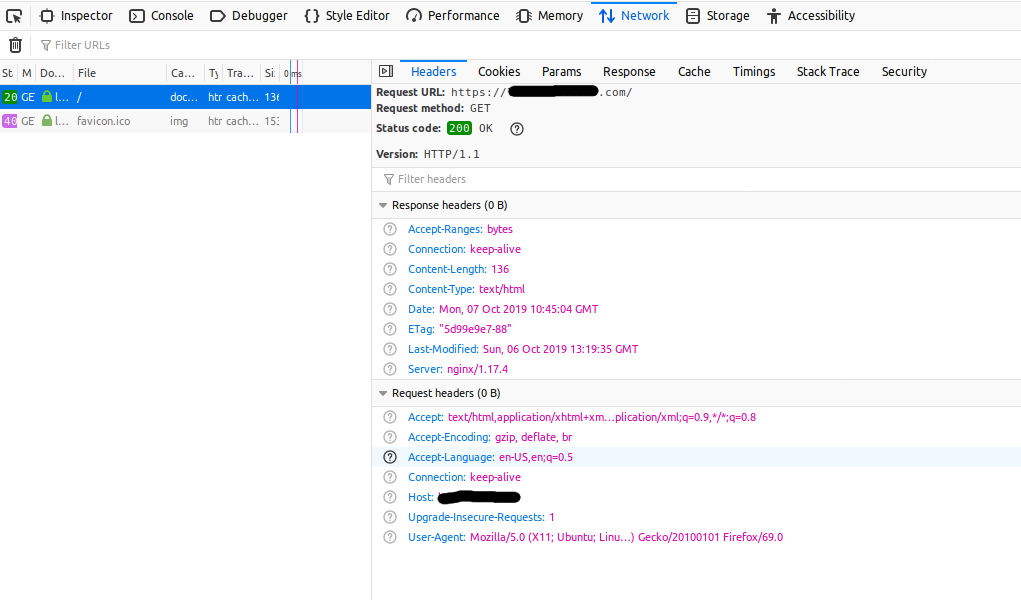
Fig 1
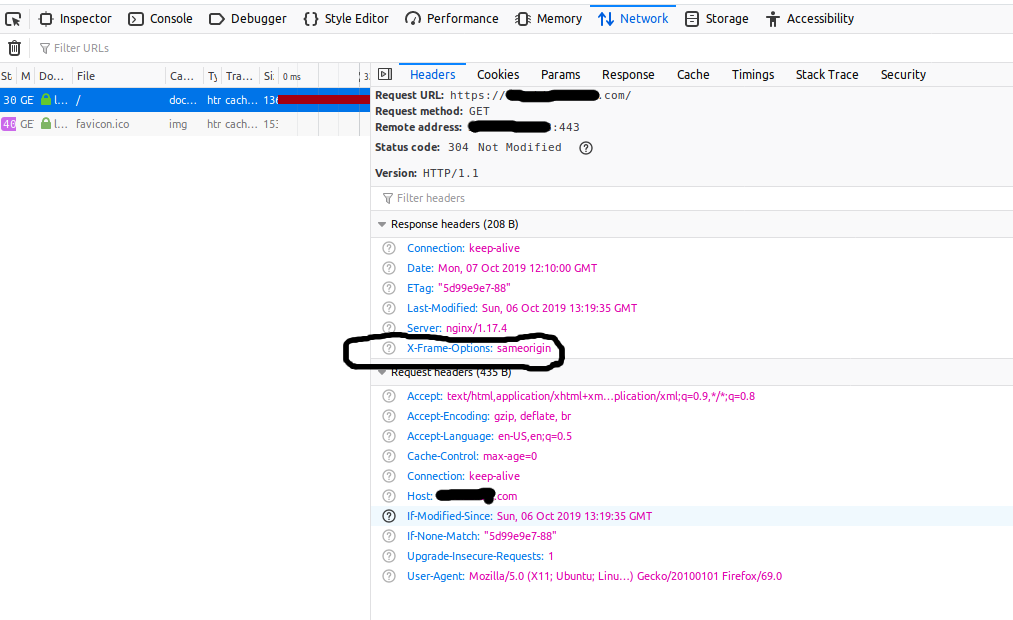
Fig 2
We can clearly see that our changes are reflected in the HTTP Header sent by the server.
DENY
It blocks displaying the page in an iframe from both the same-origin or from a different origin. We can update either of the
# Update - http, server, or location block
# X-Frame-Options
add_header X-Frame-Options deny;
Another way to completely block iframe opening other website content is as shown below.
# Update - http, server, or location block
# X-Frame-Options
add_header X-Frame-Options unset always;
The headers for both the changes are shown in Fig 3 and Fig 4.
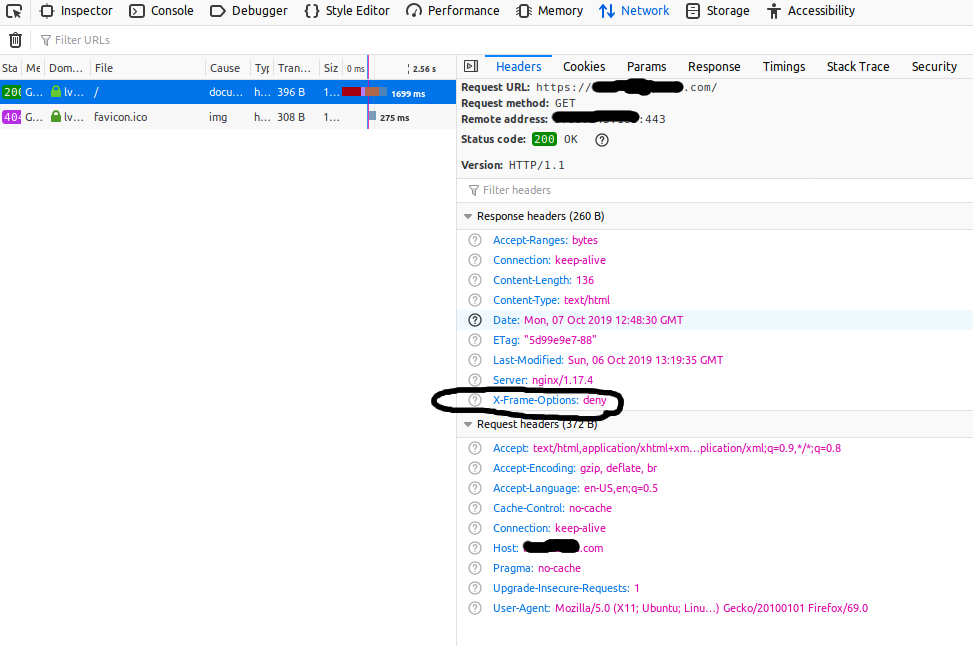
Fig 3
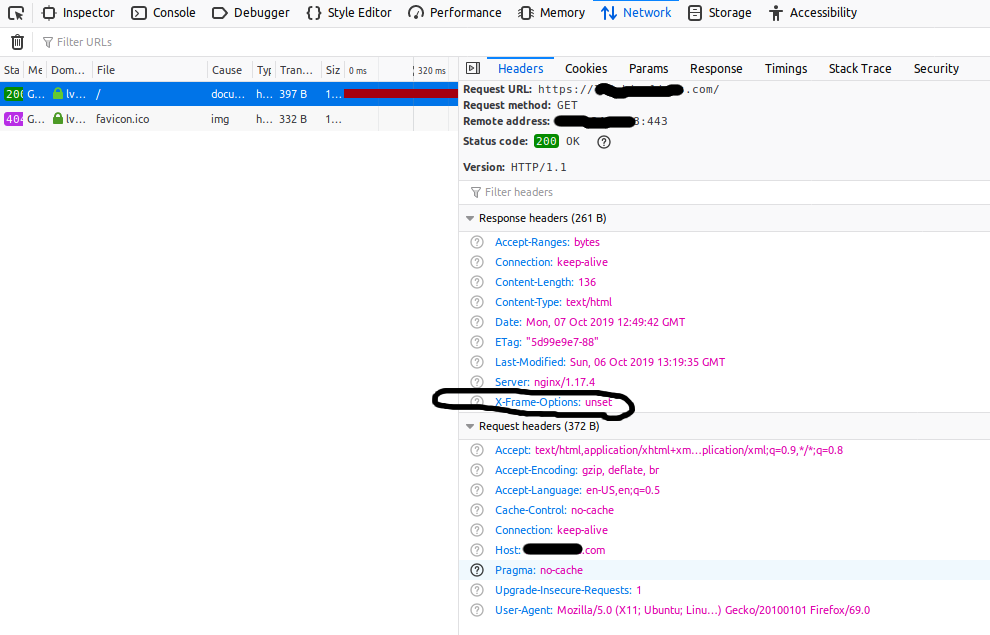
Fig 4
ALLOW-FROM
It allows specific sites to be opened in an iframe. It accepts comma separated links. This option is not supported by some of the very old browsers. It can be used as shown below.
# Update - http, server, or location block
# X-Frame-Options
add_header X-Frame-Options "ALLOW-FROM http://www.domain.com";
These are the possible options provided by X-Frame-Options to either allow or disallow frames opening content from other sites as shown in Fig 5.

Fig 5
Summary
This is how we can secure the sites or applications hosted on the Nginx Web Server from Clickjacking by using the X-Frame-Options.